Systems Audit
Incident detection and response across all hosts and end-points in any organisation requires a deep understanding of actions and behavior across users, applications, and devices. Endpoint detection and protection tools plus powerful audit and visualisation tools can provide deep insight and analysis of security-relevant events crucial to detecting and analysing advanced threats.
Aurora Networks Systems Audit
Aurora Networks Systems Audit implementation using OSQUERY, plus Host-Based IDS Service, used in conjunction with Graylog centralised logging, represent a security framework that can deliver immediate security outcomes for detection and response.
Description
OSQUERY is an open-source tool originally developed at Facebook that exposes operating system configuration data in the form of relational database tables. By issuing SQL-like queries against these tables, administrators can collect valuable data about the current state of the system as well as changes applied to it over time.
OSQUERY agents are available for all operating systems, including MS-Windows, all Linux flavors, BSDs, MacOS, etc.
Technical BrochureDownload Technical Brochure
OSQUERY Tables:
OSQUERY collects and aggregates a system’s log and status information in a collection of predefined tables. Users can interrogate the system state with SQL queries against these tables. Queries are issued either through osqueryi, an interactive SQL environment, or osqueryd, a long-lived daemon for execution of repeated, scheduled queries.
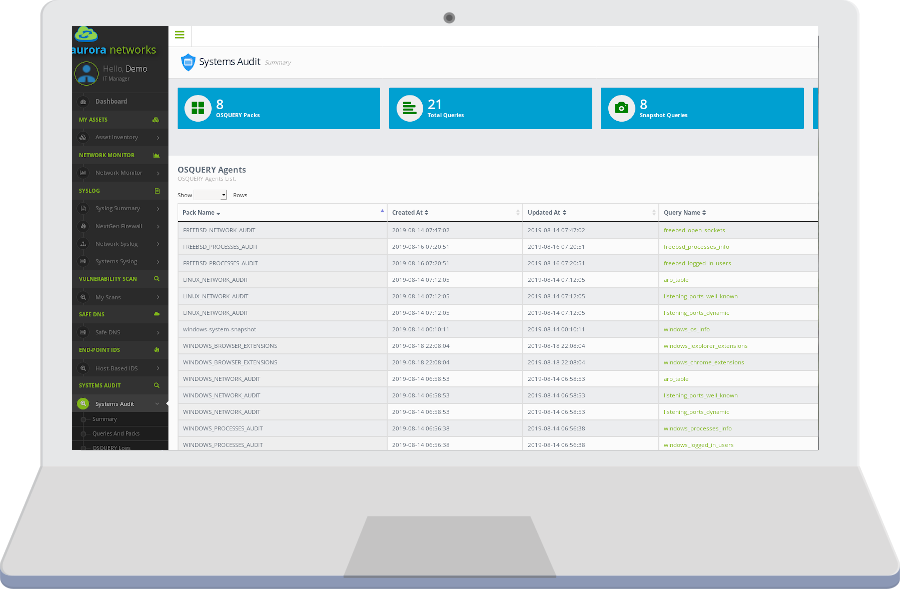
Query packs are collections of pre-defined queries that often fit into a common category. In the case of auditing windows-based machines, Aurora Networks implements the following packs:
Windows Processes Audit: System processes, system services, logon sessions (processes and services), interactive user logons.
Windows Browser Extensions: IE and Chrome extensions.
Windows Network Audit: ARP Cache, open ports (well-known), open ports (dynamic).
Windows Security Audit: Windows Update Service Status, Windows Defender Status, Windows Firewall Status, OSSEC agent status.
OSQUERY agents register with Kolide Fleet manager hosted in Aurora Networks VPC. End-point to End-point communications (agent to manager) are encrypted using TLS.
On the Kolide Fleet manager is where all the packs and queries, along with their schedule, are configured. The manager instructs each agent to execute the queries and the agent reports back to the manager their outputs.
The Kolide Fleet manager is sending all these results to Graylog for visualisation, analysis, notification and alerting.
The Mitre ATT&CK Framework compiles a series of tactics and techniques with constant update from the security community. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies.
All the queries, packs and audits implemented by Aurora Networks reflect specific techniques as detailed by the framework.
Fully integrated in your Enterprise and SIEM portals
Get full visibility on all your scan targets, scan jobs and results through your Enterprise and SIEM portals.
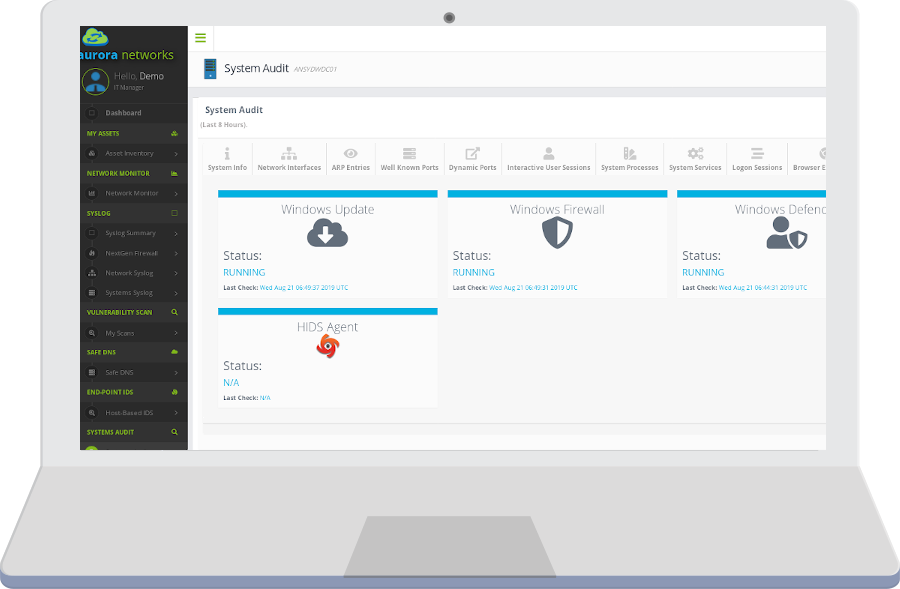
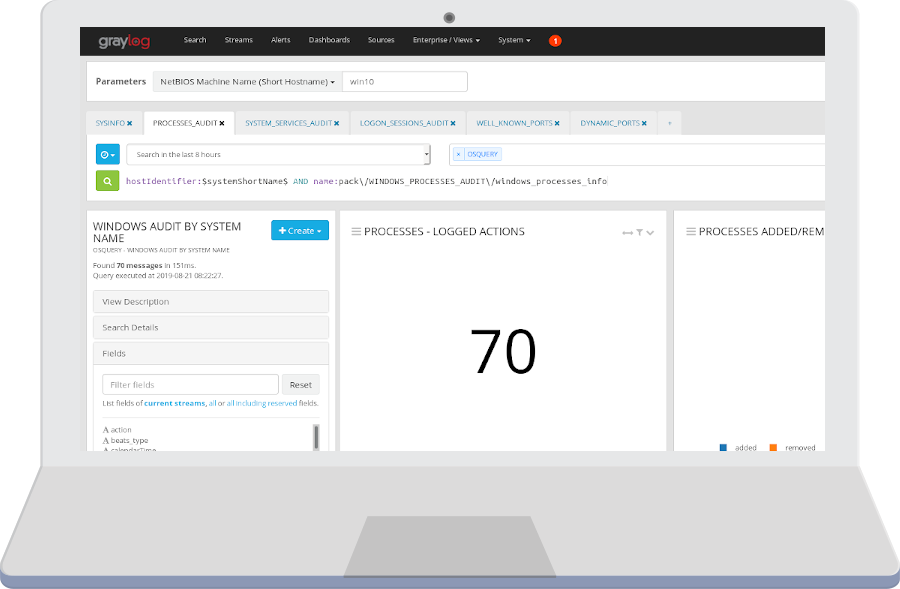
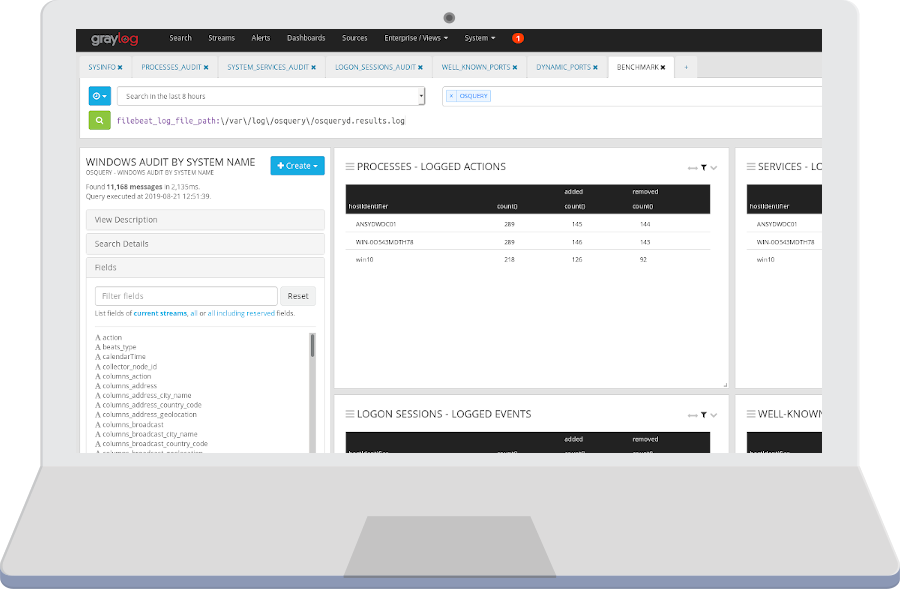
Detailed System Audit
System Processes, System Services, ARP entries, Open Sockets, etc.
Request Demo