A single solution to integrate all your network and systems logs
Rich Dashboards for instant analysis.
Centralised Log Management.
Built using Graylog’s open source solution, Aurora Networks Centralised Log Management collects, enhances, stores, and analyses ALL your log data.
Get the best of Log Management and SIEM.
Combine event data with state data and get full advantage of log management (exact insight into what happened and when) and overall state of the system (configurations, running applications, active users, processes, registry settings, and vulnerabilities).
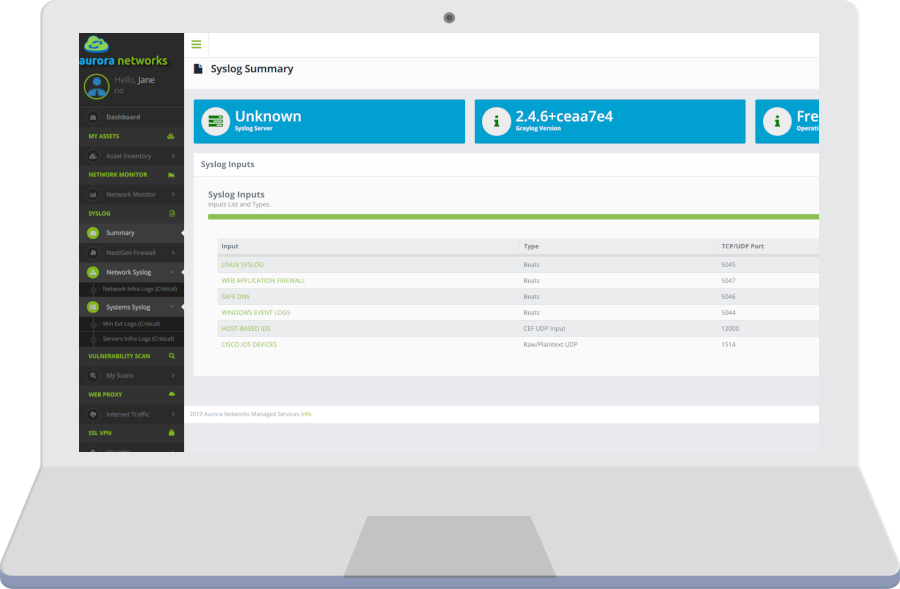
Centralised Log Management Built For Interactivity and Speed
Based on the Open-Source solution Graylog. Get all your log information, alerts and reports with a simple and intuitive GUI
Dashboards
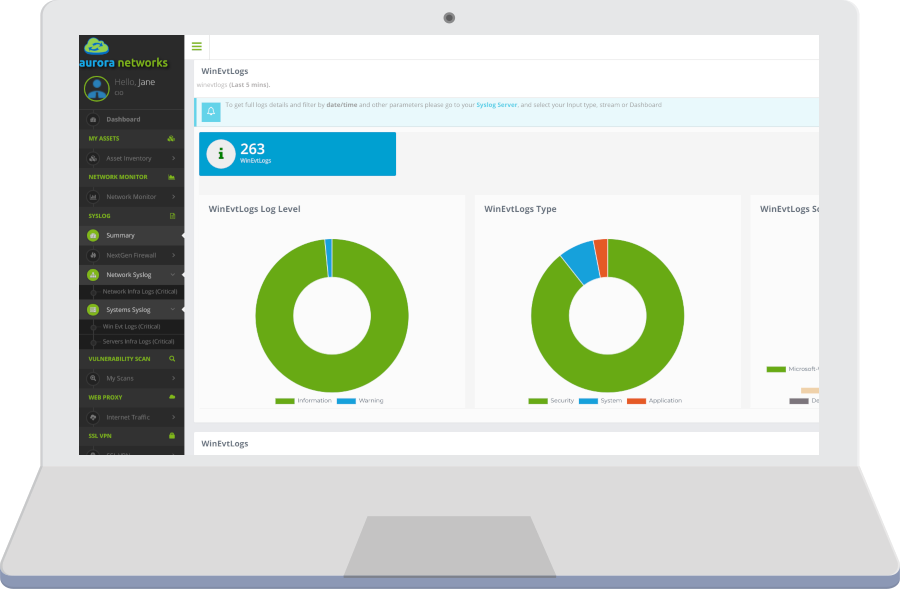
Summarised information through rich dashboards to visualise different metrics and trends on a single page. Direct access to detailed information for in-depth analysis.
Request DemoLog all your network devices and systems activity
Simple Remote syslog configuration on network devices and collector agent running in servers.
Request DemoIdentify Threats and Malicious Activity
Centralised log management that will allow you to identify threats and get alerted for more effective incident response.
Request DemoExplore Your Logs and Data In Depth
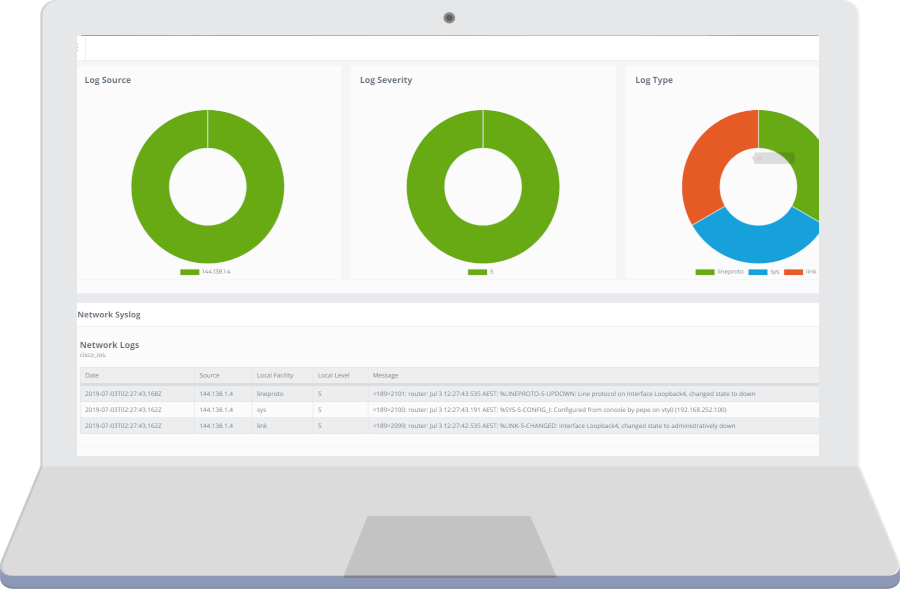
Visualise, analyse and explore all your logs and relevant data using search queries. Correlate any event by displaying additional data to find out what happened right before and after.
Request DemoCentralised Log Management and SIEM
Description
Search and Analyse Events: Flexibility to conduct analysis and event correlation. Filters help you find more granular data
Collect, parse, store, and analyse.From a single screen you can start with an input like a suspicious IP address and immediately get an overview of all connections that IP was making in the past.We set up notifications through channels such as email.
Collect, parse, store, and analyse. Enrich that data with additional information like threat intelligence data, IP geolocation, WHOIS data, and LDAP/AD information. You can even flag people and/or assets based on compliance requirements to make your reporting more robust and limit the number of systems needed to support an audit.
Once alerted, go threat hunting in seconds. From a single screen you can start with an input like a suspicious IP address and immediately get an overview of all connections that IP was making in the past. Then drill down to the targets in the organization and quickly analyze traffic patterns.
We set up notifications through channels such as email to proactively inform you of critical alarms that may indicate a system compromise or attack.